The Gist After so many outages by major cloud providers, CIOs and CTOs are remapping their cloud strategies to...
Author Archive for: Gregory Keyes
Petya Ransomware, The Land of the Fee
, Security Best Practices, Security Tech, cyber security, IT Security, network security, ransomwareThe Gist Just when businesses everywhere started recovering from the blow of the Wannacry ransomware attack, another one strikes...
Cybersecurity in a Mobile and IoT World
, Security Best Practices, Security Tech, IoT, network securityThe Gist In an age where mobile and IoT devices dominate tech, here is what you need to do...
GIST New Apple hardware and software reveals hint at the retirement of support for older, 32-bit systems. At their...
Cybersecurity, an Organization’s Immune System
, Communication Networks, Security Best Practices, Security TechThe Gist Keeping your organization’s technology on the most recent operating system is not enough. Information security professionals should develop...
Spring Clean Your Hard Drives the Safe Way
, Security Tech, Technology News, hard drives, IT Security, securityThe Gist It’s time to dump the old hard drives. Make sure you wipe them the right way with...
Encryption Ransomware, The Hostage PC
, Security Best Practices, Security Tech, cyber security, ransomware, security solutionsThe Gist Cyber criminals aren’t interested in the small fish, they’re going straight for the big guys. Targeted enterprises...
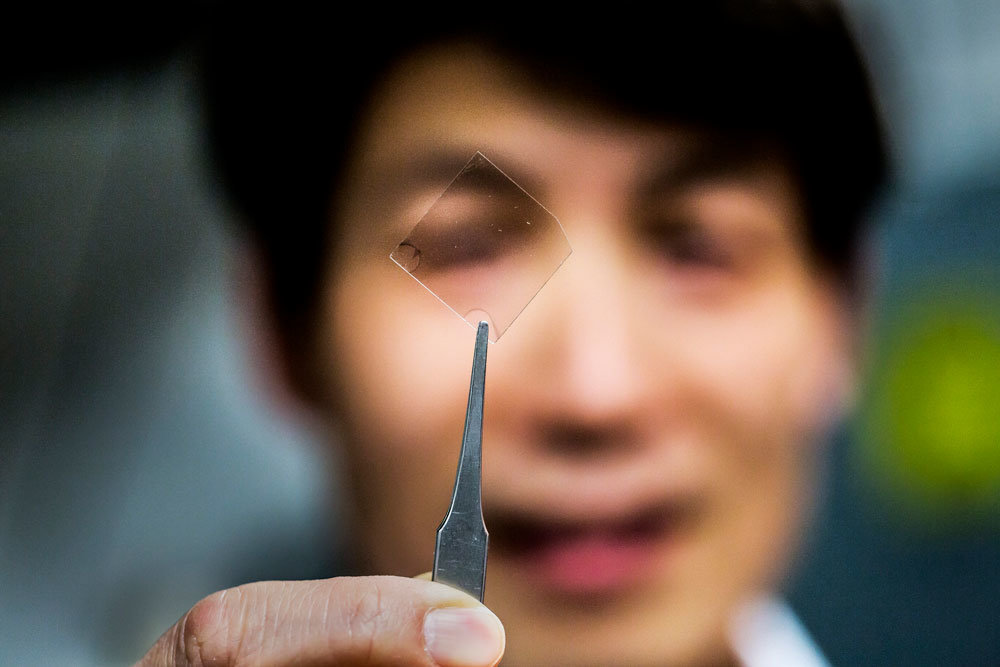
Transparent Silver, The Future of Mobile Touch Screens
, Communication Networks, Cool Tech, Technology News, cool tech, mobileThe Gist Research at the University of Michigan has found a way to use transparent layers of silver to...
The gist Automation does not mean the end of IT work. Many businesses are using automation for low-level IT...